The Mechanics of OAuth
OAuth operates under the premise of secure, delegated authorization, where user data is protected while third-party applications gain necessary permissions without direct access to credentials. This section dives into the mechanics behind OAuth, providing insights into how the protocol secures the verification process between the app and the user, and how it leverages access tokens and authorization codes to maintain security standards.
Resource Owner
|
| 1. Authorize
v
+--------------+ +-------------------+
| | | |
| Authorization|----------->| Authorization |
| Server | 2. Grant | Server |
| |<-----------| |
+--------------+ +-------------------+
^ | |
| | 3. Access Token | 4. Validate
| v v
+--------------+ +-------------------+
| | | |
| Client |----------->| Resource |
| | 5. Request | Server |
| |<-----------| |
+--------------+ 6. Resource+-------------------+
The Functioning of OAuth: App and User Verification
The verification in OAuth involves multiple entities: the client application, the authorization server, and the resource owner. To illustrate, when a user wants to use a new email client that needs access to their contacts,
- The client application identifies itself with a
client IDand, depending on the security level required, aclient secret. - The user authenticates with the server hosting their data, proving their identity typically through a login screen.
- Post authentication, OAuth's authorization grant type influences the exchange. For instance, the
authorization code flowis utilized for applications that can guard a client secret. - The authorization server validates the request and prompts the user with a permission grant screen. User consent is critical.
- Upon consent, a code is issued to the application. The code is an intermediate token; it's not the final key.
This sequence safeguards user data, granting access without exposing sensitive information. The entire process embeds several checks to ensure both the application and the user are genuine, the paramount step being the exchange of credentials and codes via secure channels.
Understanding Access Tokens and Authorization Code in OAuth2.0
OAuth2.0's elegance is encapsulated in its use of access tokens and authorization codes:
-
Authorization Codes are short-lived tokens exchanged for an access token. They're transmitted back to the client application after the initial user consent via a callback URI.
-
Access Tokens:
- Are akin to a valet key for your digital resources.
- Come with a defined scope, type of access, and expiration time.
- Authenticate sessions and requests for the target resources, without revealing the user's identity or credentials.
Here's a simplified breakdown of the token flow in OAuth 2.0:
- Authorization Request: The user agrees to the login attempt, prompting the server to issue an authorization code.
- Token Exchange: The client exchanges the authorization code for an
access token. - Resource Access: Using the access token, the client requests access to the resource server.
- Token Validation: The resource server validates the access token and, if legitimate, allows the requested action.
By separating the initial grant from the token that actually allows access, OAuth 2.0 adds a robust layer of security, ensuring that even if an authorization code is intercepted, the thief would also need access to the client application and its credentials to gain any further access.
Advancement in OAuth: From 1.0 to 2.0
OAuth has undergone significant evolution from its inception to its current state, where OAuth 2.0 is the widely adopted standard. The advancements from OAuth 1.0 to 2.0 reflect a maturation that has targeted ease of use, flexibility, and improved security measures, making it an integral component of modern web and application development.
Highlighting the Differences Between OAuth 1.0 and 2.0
The transition from OAuth 1.0 to OAuth 2.0 introduced key changes that enhance functionality and developer experience. OAuth 2.0 streamlines the process of securing authorization in several critical ways:
- Simplified Client Development: OAuth 2.0 removed cryptographic requirements like signatures, simplifying client development.
- Enhanced Flexibility: The introduction of multiple grant types in OAuth 2.0 added versatility for different scenarios.
- Short-lived Tokens: OAuth 2.0 focused on the use of short-lived access tokens, increasing security through limited access duration.
- Scalability with Tokens: The tokens in OAuth 2.0 are specific to the client's requested scope, making the protocol scalable and more secure.
Diving into the specifics, OAuth 2.0 provides developers with options like bearer tokens and consent frameworks that weren't available or standardized in OAuth 1.0.
Evolution of OAuth and Current Standards
As OAuth evolved, its implementation and standards saw continuous updates, keeping pace with emerging technologies and security concerns. The current standards in OAuth encompass:
- PKCE (Proof Key for Code Exchange) added to OAuth 2.0, enhancing security for mobile and single-page applications.
- OAuth 2.1: A draft proposal consolidating best practices, aiming to simplify the protocol and phase out deprecated features like the Implicit grant.
The evolution points to a more streamlined and secure approach to authorization, ensuring that OAuth remains relevant and robust against new security challenges.
OAuth1.0 vs OAuth2.0: Security Enhancements
Security has always been paramount in OAuth's design, and OAuth 2.0 has implemented considerable enhancements over its predecessor:
- OAuth 2.0 provides the ability to use refresh tokens, allowing applications to maintain access without repeated user logins, which reduces the attack surface.
- The protocol removed the reliance on signatures and introduced the use of TLS, which modernized and simplified securing communication between the client and server.
- The granularity of access control in OAuth 2.0 means more precise permission levels, promoting the principle of least privilege.
Here is how refresh token comes into play.
Resource Owner
|
| 1. Authorize
v
+--------------+ +-------------------+
| | | |
| Authorization|----------->| Authorization |
| Server | 2. Grant | Server |
| |<-----------| |
+--------------+ +-------------------+
^ | |
| | 3. Access Token + Refresh Token| 4. Validate
| v v
+--------------+ +-------------------+
| | | |
| Client |----------->| Resource |
| | 5. Request | Server |
| |<-----------| |
+--------------+ 6. Resource+-------------------+
| ^
| 7. Refresh Token |
v |
+--------------+ +-------------------+
| | | |
| Authorization|<-----------| Authorization |
| Server | 8. New Access Token | Server |
| |----------->| |
+--------------+ +-------------------+While OAuth 2.0 isn't flawless and has faced scrutiny, its adoption and ongoing improvements solidify its standing as a secure authorization protocol up to present-day demands.
OAuth as a Secure Authorization Protocol
OAuth stands at the forefront of secure, robust authorization protocols for today's web and native applications. Crystallizing user trust with a flow seamless for developers and consumers alike, OAuth has revolutionized how we share permissions without compromising credentials.
The Benefit of Standard and Simplified Authorization
OAuth eliminates the complexities once bogging down authorization. With standard claims and tokens, OAuth streamlines the login process. Imagine a mobile application requesting access to your email; instead of providing your email password, an access token is used. This is the OAuth advantage: it standardizes and simplifies user consent into reliable steps.
Securing Access to Web, Mobile, and Desktop Applications
OAuth bolsters security across device landscapes—be it browsers, mobile apps, or desktop applications. By handling user credentials with utmost confidentiality, OAuth prevents direct access to user passwords. This ensures a barricade against unauthorized access, securing each application type against numerous security flaws inherent in traditional password-based systems.
OAuth and Other Standards: Comparisons and Contrasts
OAuth emerges distinctly when weighed against other standards. It advances over simple password transmissions by employing tokens, which can be restricted in scope and have an expiration, contrasting sharply with potentially perennial and all-encompassing passwords. Moreover, compared to SAML and other identity-centric authorization protocols, OAuth shines in delegated access, where an application acts on behalf of the user with their explicit consent.
Types of Grant in OAuth 2.0
OAuth 2.0 introduces a spectrum of grant types designed to cater to different application scenarios and security requirements. Understanding these grant types is essential for implementing OAuth effectively, as each serves a unique purpose and operates under distinct conditions.
Exploring the Resource Owner's Password Credentials Grant
Resource Owner Password Credentials Grant is straightforward: it involves the direct exchange of user credentials for an access token. This is less common because it requires users to trust the application with their passwords, potentially exposing sensitive information. It's typically used by clients that are highly trusted by the user, such as those developed by the service provider itself.
Steps for Resource Owner's Password Credentials Grant:
- The user enters their username and password into the client application.
- The client application sends these credentials to the authorization server.
- If the credentials are valid, an access token (and optionally a refresh token) is issued to the client.
Despite its simplicity, due to security concerns, this grant type is generally recommended only when other, more secure methods are not feasible.
Unraveling the Client Credentials Grant
The Client Credentials Grant is utilized when the client is also the resource owner or is acting on its own behalf rather than an external user. It's common in server-to-server communications where no user interaction is involved.
For this grant type:
- The client presents its own credentials – a client ID and client secret.
- The authorization server authenticates the client and issues an access token.
The simplicity here lies in the non-requirement of user interaction, streamlined for automated systems and backend services.
Comprehending the Authorization Code Grant
The Authorization Code Grant is a versatile and secure grant type, well-suited for clients capable of maintaining the confidentiality of the client secret. It is the preferred method for applications able to securely store secrets and is ideal for server-side web applications.
The flow typically involves:
- Redirecting the user to a login screen and then to a consent screen.
- Issuing a short-lived authorization code upon user consent.
- The client exchanging this code for an access token.
This grant type further separates the user's credentials from the application, adding an extra layer of security.
Demystifying the Implicit Grant in OAuth 2.0
The Implicit Grant was designed for scenarios where the application is unable to securely store a client secret due to client-side constraints, such as in single-page applications. It streamlines the process by issuing an access token directly after the authorization request.
Key points for Implicit Grant:
- User authorization translates immediately into an access token.
- No intermediate authorization code is generated, simplifying the flow.
However, the Implicit Grant is less secure than the Authorization Code Grant, leading to its deprecation in OAuth 2.1 because the access token is exposed in the redirect URI, which could be intercepted by malicious parties.
Differentiating OAuth Scopes and Roles
The OAuth framework is a web of interactions between various scopes and roles that determine the extent to which applications can access user data and the participants in the authorization process. Scopes define the boundaries of permission, while roles clarify the responsibilities and actions of the parties involved in the OAuth flow.
OAuth2.0 Scopes and Applications
In OAuth 2.0, scopes are utilized to specify the level of access that applications request for user resources. They are a vital mechanism for user control, granting granular permission levels to the client application. A well-defined scope ensures that applications do not overstep the access granted by the user.
Consider scopes as access levels in a building, illustrated as follows:
[Application]
||
Scope /-----||-----\
Access || || ||
Levels V V V
-----------------
Floor 3 | Email | Calendar | Drive |
-----------------
Floor 2 | Contacts| Photos | Docs |
-----------------
Floor 1 | Profile | Settings | Billing|
-----------------Each "floor" represents a different scope level—asking for the "email" scope is like requesting access to the third floor, allowing the application to interact only with email-related resources.
Unpacking OAuth2.0 Roles
OAuth 2.0 roles include:
- Resource Owner: The user who authorizes an application to access their resources.
- Client: The application requesting access to the user's resources.
- Authorization Server: The server that authenticates the resource owner and issues access tokens.
- Resource Server: The server hosting user resources that accepts and responds to protected resource requests.
Each role has its own responsibilities in the authorization framework, ensuring clear separation of concerns.
Understanding Applications that Support the Auth Code Flow
Applications that support the Authorization Code flow are typically those that can maintain the confidentiality of client secrets—server-side web applications are a prime example. This flow is a secure method utilized by clients, including enterprise apps and commercial software, that seek to access protected resources by obtaining an authorization code.
Here's an illustration of the Auth Code Flow:
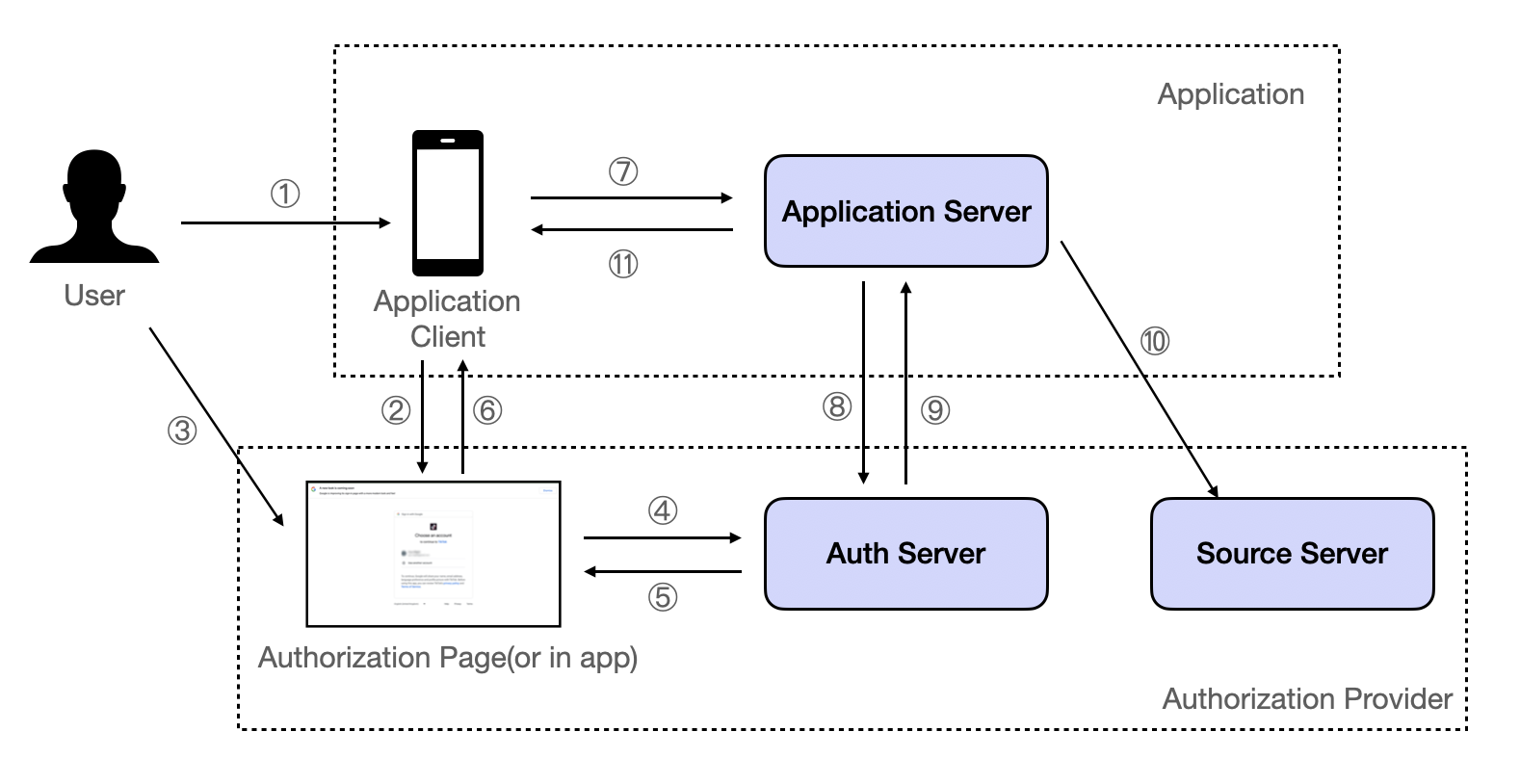
In this flow:
① The user initiates third-party login;
② The Application Client opens an Authorization page or launches the Authorization Provider's App, waiting for the user to take action;
③ The user consents;
④ The Authorization page notifies the Auth Server that "the user has consented";
⑤ The Authorization Server responds back with a single-use authorization code;
⑥ The Authorization page passes the single-use authorization code back to the Application Client;
⑦ The Application Client sends the previously obtained single-use authorization code to the Application Server;
⑧ The Application Server sends the single-use authorization code to the Auth Server for verification;
⑨ After successfully verifying the single-use authorization code, the Authorization Server responds with an ID token and access token (and optionally, a refresh token);
⑩ The Application Server can use the access token to request authorized resources from the Source Server, such as nickname, avatar, personal profile, etc.;
⑪ The Application Server sends the necessary authorization information to the Application Client (this is customized and not part of the OAuth scope).
OAuth in Action: Cases and Examples
OAuth is not a theoretical construct; it's a protocol in constant use across the digital landscape. It facilitates secure interactions in multitudinous scenarios, from third-party service authorizations to single-page applications. Let's explore some practical cases and examples where OAuth simplifies and secures authorization.
Third-party Service Authorization Using OAuth
When users leverage a third-party service like a social media management tool to post to their accounts, OAuth springs into action. The tool needs access to user's social media but should not possess the password. Here's a simplified code example of how this third party can retrieve an access token, using Python with the requests library:
import requests
# Define the client credentials and authorization URI
client_id = 'your-client-id'
client_secret = 'your-client-secret'
authorization_url = 'https://authorization-server.com/auth'
# Direct user to authorization URI
redirect_uri = 'https://your-redirect-uri.com/callback'
scope = 'write_post'
print(f"Please go to {authorization_url} and authorize access.")
# Exchange authorization code for access token
auth_code = 'authorization-code' # This code would be retrieved from the redirect URI query params
token_url = 'https://authorization-server.com/token'
token_response = requests.post(
token_url,
data={
'grant_type': 'authorization_code',
'code': auth_code,
'redirect_uri': redirect_uri,
'client_id': client_id,
'client_secret': client_secret
}
)
access_token = token_response.json().get('access_token')First-party Service Authorization with OAuth
First-party applications can also use OAuth to authenticate and authorize users. For example, a mobile banking app requiring access to the bank's API. Below is a code example using JavaScript's fetch API:
// Set up the data with client credentials
const data = new URLSearchParams({
client_id: "your-client-id",
client_secret: "your-client-secret",
grant_type: "password",
username: "user@example.com",
password: "user-password",
});
// API endpoint for the bank's OAuth 2.0 server
const tokenUrl = "https://bank-oauth2-server.com/token";
// Fetch the access token
fetch(tokenUrl, {
method: "POST",
body: data,
})
.then((response) => response.json())
.then((data) => {
// Now you have the access token
console.log("Access Token:", data.access_token);
});Exploring Single-Page App (SPA) Use Cases
Single-page applications (SPAs) often need to access APIs for dynamic content without reloading the webpage. They can utilize OAuth's Implicit Grant flow (less recommended nowadays) or opt for the Authorization Code flow with PKCE. Here’s how a SPA might initiate an Authorization Code flow with PKCE using JavaScript:
// Example using the new authorization code with PKCE flow
const codeVerifier = code_verifier_generation_function();
const codeChallenge = code_challenge_generation_function(codeVerifier);
const authorizationUrl = new URL("https://authorization-server.com/auth");
authorizationUrl.searchParams.append("client_id", "your-client-id");
authorizationUrl.searchParams.append("response_type", "code");
authorizationUrl.searchParams.append(
"redirect_uri",
"https://your-spa.com/callback"
);
authorizationUrl.searchParams.append("code_challenge", codeChallenge);
authorizationUrl.searchParams.append("code_challenge_method", "S256");
authorizationUrl.searchParams.append("scope", "read_profile");
// Redirect the user to the authorization server
window.location = authorizationUrl;In each of these examples, OAuth stands as the enforcing agent of security, ensuring that permissions are given explicitly by the user and with limitations that protect their privacy and data integrity.
Key Takeaways
Through the intricate workings of OAuth 2.0, we glean invaluable lessons, concepts, and real-world applications that underscore the protocol’s significance. As we distill the information, let us crystallize the most pivotal insights for practical application and a deeper understanding of OAuth 2.0’s utility in the digital landscape.
Lessons on OAuth 2.0 Best Practices
Best practices in OAuth 2.0 are foundational to secure and effective authorization:
- Securely Store Credentials: Client secrets must be kept confidential to prevent unauthorized access.
- Use TLS: Transport Layer Security (TLS) should be enforced to encrypt communication.
- Adopt PKCE: Especially for public clients, PKCE mitigates the risk of code interception attacks.
- Limit Scope: Only request access to the necessary scopes to minimize potential data exposure.
- Regularly Refresh Tokens: Utilize refresh tokens to maintain access without re-prompting users for credentials.
Implementing these measures will fortify your OAuth implementation against common threats.
Understanding OAuth 2.0 Concepts for Better Application
A robust understanding of OAuth 2.0 is critical for developing secure applications that handle user data responsibly:
- Know Your Roles: Differentiate between the client, resource owner, authorization server, and resource server.
- Choose the Right Grant Type: Select the grant type that matches your application type and security requirements.
- Implement Consents Properly: Ensure that user consents are informed and specific to enhance trust and compliance.
Grasping these concepts thoroughly equips software engineers to craft superior and secure authorization flows.
Observing Use Cases and Real-World Applications
Examining OAuth in the wild provides a practical perspective on its capabilities:
- Third-party Integrations: Whether it's social media platforms or data analysis tools, OAuth is the go-to for secure third-party service authorization.
- First-party Authentication: Enterprises leverage OAuth for secure internal application access, minimizing risks inherent in traditional authentication methods.
- Modern Web Applications: OAuth facilitates dynamic client-side applications like SPAs, enabling secure API requests without page reloads.
By observing these use cases, developers gain insights into effective OAuth implementations that safeguard user data across diverse platforms and applications.
Frequently Asked Questions
Navigating OAuth can present a variety of questions as developers implement this essential protocol. Below are answers to some common inquiries surrounding OAuth's mechanisms, from the utility of refresh tokens to the role of scopes and addressing typical error messages.
What is the Purpose of Refresh Token in OAuth?
The refresh token in OAuth plays a critical role in maintaining a user's session without asking them to repeatedly enter their credentials:
- Longevity: Refresh tokens have a longer lifespan than access tokens.
- Security: They minimize the risk of access tokens being captured since they're not repeatedly transported.
- Convenience: Users experience fewer interruptions due to session expirations.
Use refresh tokens wisely by storing them securely and issuing new ones each time an access token is renewed, a practice known as "token rotation."
How are OAuth Scopes Utilized in Software Engineering?
In software engineering, OAuth scopes define the extent of access an application is granted:
- Data Protection: Scopes limit what data an application can request, aligning with the principle of least privilege.
- User Control: They allow users to precisely control their data sharing and permissions.
- Flexibility: Developers can tailor experiences based on granted permissions.
When designing an application, carefully consider and document the scopes needed for the required functionality.
What are Some Common Error Codes and How Can They Be Resolved?
Errors are a regular part of any authentication flow, and OAuth provides specific codes to indicate certain issues:
invalid_request: Check whether the request is missing parameters or is malformed.invalid_client: Ensure the client ID and secret are correct and properly authenticated.invalid_grant: This might indicate an expired grant or refresh token, or a reused authorization code.unauthorized_client: The client is not authorized to use the requested grant type.access_denied: The resource owner or authorization server denied the request.
Resolving these errors typically involves adjusting request parameters, reauthenticating credentials, or managing tokens more carefully. When an error occurs, use its code as a guide to troubleshoot and rectify the issue efficiently.